Current and Recent Research Projects
Security of Programmable Network Data Planes
Collaborators: Purdue University, Rice University, University of Michigan, University of Waterloo, Illinois Institute of Technology, and SRI International
Summary
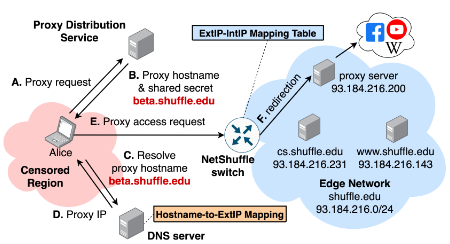
Programmable data planes, such as Programming Protocol-independent Packet Processors (P4), ofter new flexibility in terms of extending the control plane functionality of networks into the fast path hardware of the data plane. Such programmability enables new protocol development (e.g., non-IP-based networks) and provides new ways of enabling high-performance computational tasks that would have previously required expensive control plane resources. However, such programmability creates new threat vectors that require further exploration to fully realize all of the benefits that programmable data planes have to offer.
This project broadly aims to understand how the programmable data plane infrastructure affects the overall security posture of the network and how such capabilities can further enhance network device security capabilities (e.g., threat monitoring, intrusion detection, privacy enhancement, etc.). Using program analysis methodologies, we are investigating novel attacks and devising analysis techniques for the P4 language and infrastructure that are uniquely tailored to programmable data plane semantics. We are also investigating how P4 infrastructure can further enhance existing network security capabilities in novel ways (e.g., moving target defenses).
Papers
- Several papers are in submission or forthcoming. Please contact for more information.
- “NetShuffle: Circumventing Censorship with Shuffle Proxies at the Edge” (IEEE link)
Patrick Tser Jern Kon, Aniket Gattani, Dhiraj Saharia, Tianyu Cao, Diogo Barradas, Ang Chen, Micah Sherr, and Benjamin E. Ujcich
2024 IEEE Symposium on Security & Privacy (S&P/Oakland ‘24)
Acceptance rate: TBD
San Francisco, California, USA, 20-22 May 2024
Code
- NetShuffle repo: https://github.com/patrickkon/NetShuffle
Security of Intent-Based Networking
Collaborators: Purdue University, MIT Lincoln Laboratory, and Northeastern University
Summary
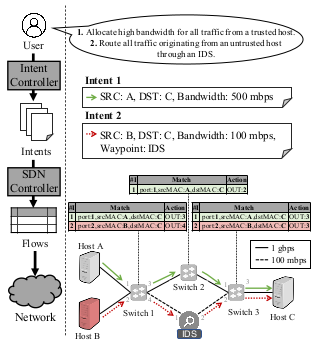
Intent-based networking (IBN) promises to ease network management challenges for practitioners by abstracting away the increasingly complex details about network configuration, protocols, and topology. Rather than relying on low-level configuration changes, practitioners can declaratively specify their intents of what they want the network to do, not how to achieve it. IBN is set to see increased adoption in the coming years with machine-learning approaches that automatically configure the network. While providing significant management benefits, IBN creates new security challenges as underlying implementations, configurations, topologies, and protocols are abstracted away from the practitioner.
This project broadly aims to understand the security implications of the intent-based networking architecture. Within IBN, we are investigating efficient methods for discovering vulnerabilities, verifying network segmentation and isolation properties, enforcing access control, enhancing root cause analysis, and analyzing cross-layer/cross-domain security challenges (e.g., interactions with IoT).
Papers
- Several papers are in submission or forthcoming. Please contact for more information.
- “Exploiting Temporal Vulnerabilities for Unauthorized Access in Intent-Based Networking” (ACM link)
Ben Weintraub, Jiwon Kim, Ran Tao, Cristina Nita-Rotaru, Hamed Okhravi, Dave (Jing) Tian, and Benjamin E. Ujcich
2024 ACM Conference on Computer and Communications Security (CCS ‘24)
Acceptance rate: TBD
Salt Lake City, Utah, USA, 14-18 October 2024 - “Security Challenges of Intent-Based Networking” (CACM link) (ACM link)
Jiwon Kim, Dave (Jing) Tian, Hamed Okhravi, and Benjamin E. Ujcich
Communications of the ACM, July 2024. - “Intender: Fuzzing Intent-Based Networking with Intent-State Transition Guidance” (USENIX link)
Jiwon Kim, Benjamin E. Ujcich, and Dave (Jing) Tian
2023 USENIX Security Symposium (Security ‘23)
Acceptance rate: TBD
Anaheim, California, USA, 9-11 August 2023 - “Provenance for Intent-Based Networking” (IEEE link)
Benjamin E. Ujcich, Adam Bates, and William H. Sanders
2020 IEEE Conference on Network Softwarization (NetSoft ‘20)
Ghent, Belgium (virtual), 29 June - 3 July 2020
Code
- Spotlight repo: https://zenodo.org/records/12735280
- Intender repo: https://github.com/purseclab/intender
Security of Network Orchestrators
Collaborators: Purdue University
Summary
Network orchestrators, such as the Linux Foundation’s Open Network Automation Platform (ONAP), coordinate and provision (virtual) network resources within a network and increasingly play a key role in enabling scalable and secure future 5G / 6G / next-generation network architectures. In contrast to traditional networks, such networks must deal with multi-tenant performance and security challenges and multi-operator trust challenges. Given the complexity of the orchestration software itself, practitioners also face concerns about the security of their deployment and often must assume zero-trust postures.
This project aims to understand how the complexity of network orchestration systems impacts the underlying security properties of future networks. We are investigating new methods for being able to reason about the control and management decisions made by network orchestrators in terms of data plane, control plane, management plane, end host and domain-specific applications.
Papers
- Several papers are in submission or forthcoming. Please contact for more information.
Security of Programmable Network Control Planes
Root Cause Analysis for Programmable Network Attacks
Collaborators: University of Illinois at Urbana-Champaign, Carnegie Mellon University, and MIT Lincoln Laboratory
Summary
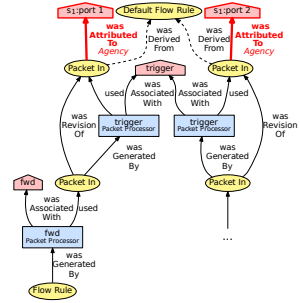
Software-defined networking (SDN) has emerged as a flexible network architecture for central and programmatic control. Although SDN can improve network security oversight and policy enforcement, ensuring the security of SDN from sophisticated attacks is an ongoing challenge for practitioners. Existing network forensics tools attempt to identify and track such attacks, but holistic causal reasoning across control and data planes remains challenging.
We developed PicoSDN, a provenance-informed causal observer for SDN attack analysis. PicoSDN leverages fine-grained data and execution partitioning techniques, as well as a unified control and data plane model, to allow practitioners to efficiently determine root causes of attacks and to make informed decisions on mitigating them. We implemented PicoSDN on the popular ONOS SDN controller. Our evaluation across several attack case studies shows that PicoSDN is practical for the identification, analysis, and mitigation of SDN attacks.
Papers
- “Causal Analysis for Software-Defined Networking Attacks” (USENIX link)
Benjamin E. Ujcich, Samuel Jero, Richard Skowyra, Adam Bates, William H. Sanders, and Hamed Okhravi
2021 USENIX Security Symposium (Security ‘21)
Vancouver, British Columbia, Canada (virtual), 11-13 August 2021
Code
- PicoSDN repo: https://github.com/bujcich/PicoSDN
Automated Vulnerability Discovery in Programmable Networks
Collaborators: University of Illinois at Urbana-Champaign and MIT Lincoln Laboratory
Summary
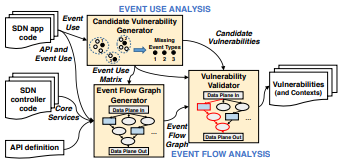
Software-defined networking (SDN) achieves a programmable control plane through the use of logically centralized, event-driven controllers and through network applications (apps) that extend the controllers’ functionality. As control plane decisions are often based on the data plane, it is possible for carefully crafted malicious data plane inputs to direct the control plane towards unwanted states that bypass network security restrictions (i.e., cross-plane attacks). Unfortunately, because of the complex interplay among controllers, apps, and data plane inputs, at present it is difficult to systematically identify and analyze these cross-plane vulnerabilities.
EventScope is a vulnerability detection tool that automatically analyzes SDN control plane event usage, discovers candidate vulnerabilities based on missing event-handling routines, and validates vulnerabilities based on data plane effects. To accurately detect missing event handlers without ground truth or developer aid, we cluster apps according to similar event usage and mark inconsistencies as candidates. We create an event flow graph to observe a global view of events and control flows within the control plane and use it to validate vulnerabilities that affect the data plane. We applied EventScope to the ONOS SDN controller and uncovered 14 new vulnerabilities.
Papers
- “Automated Discovery of Cross-Plane Event-Based Vulnerabilities in Software-Defined Networking”
(slides) (NDSS
link)
Benjamin E. Ujcich, Samuel Jero, Richard Skowyra, Steven R. Gomez, Adam Bates, William H. Sanders, and Hamed Okhravi
2020 ISOC Network and Distributed System Security Symposium (NDSS ‘20)
Code
- EventScope repo: https://github.com/bujcich/EventScope
Information Flow Control in Software-Defined Networking
Collaborators: University of Illinois at Urbana-Champaign, Northeastern University, Purdue University, Princeton University, and MIT Lincoln Laboratory
Summary
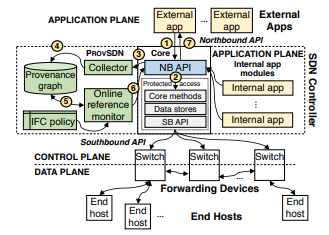
Software-defined networking (SDN) continues to grow in popularity because of its programmable and extensible control plane realized through network applications (apps). However, apps introduce significant security challenges that can systemically disrupt network operations, since apps must access or modify data in a shared control plane state. If our understanding of how such data propagate within the control plane is inadequate, apps can co-opt other apps, causing them to poison the control plane’s integrity.
We discovered a class of SDN control plane integrity attacks that we call cross-app poisoning (CAP), in which an unprivileged app manipulates the shared control plane state to trick a privileged app into taking actions on its behalf. We demonstrated how role-based access control (RBAC) schemes are insufficient for preventing such attacks because they neither track information flow nor enforce information flow control (IFC). We also presented a defense, ProvSDN, that uses data provenance to track information flow and serves as an online reference monitor to prevent CAP attacks. We implemented ProvSDN on the ONOS SDN controller and demonstrated that information flow can be tracked with low-latency overheads.
Papers
- “Cross-App Poisoning in Software-Defined Networking” (slides) (ACM link)
Benjamin E. Ujcich, Samuel Jero, Anne Edmundson, Qi Wang, Richard Skowyra, James Landry, Adam Bates, William H. Sanders, Cristina Nita-Rotaru, and Hamed Okhravi
2018 ACM Conference on Computer and Communications Security (CCS ‘18)